One Weak Password Can Break Your Website: Here’s How to Prevent It
Introduction
It only takes one weak password to undo months—or even years—of hard work on your website.
Whether you run a small business site, a personal blog, or a large e-commerce platform, login credentials are often the first and easiest target for attackers. In fact, compromised passwords remain one of the leading causes of website breaches worldwide. Hackers don’t need sophisticated tools if a password is easy to guess, reused, or poorly protected.
The good news? Most password-related attacks are entirely preventable.
In this guide, you’ll learn exactly how one weak password can break your website, what attackers look for, and—most importantly—a step-by-step approach to preventing it. We’ll keep things practical, beginner-friendly, and rooted in proven security best practices.
Why One Weak Password Is All It Takes
Attackers rarely “hack” websites the way movies portray. Instead, they rely on predictable human behavior:
-
Reusing the same password across multiple sites
-
Choosing short or common passwords
-
Skipping extra security layers like two-factor authentication
Once a hacker gains access to a single admin, FTP, or database account, they can:
-
Deface or delete your website
-
Steal user data and passwords
-
Inject malware or spam
-
Lock you out of your own site
-
Damage your reputation and SEO rankings
In many cases, website owners don’t realize what happened until search engines flag the site, customers complain, or hosting providers suspend access.
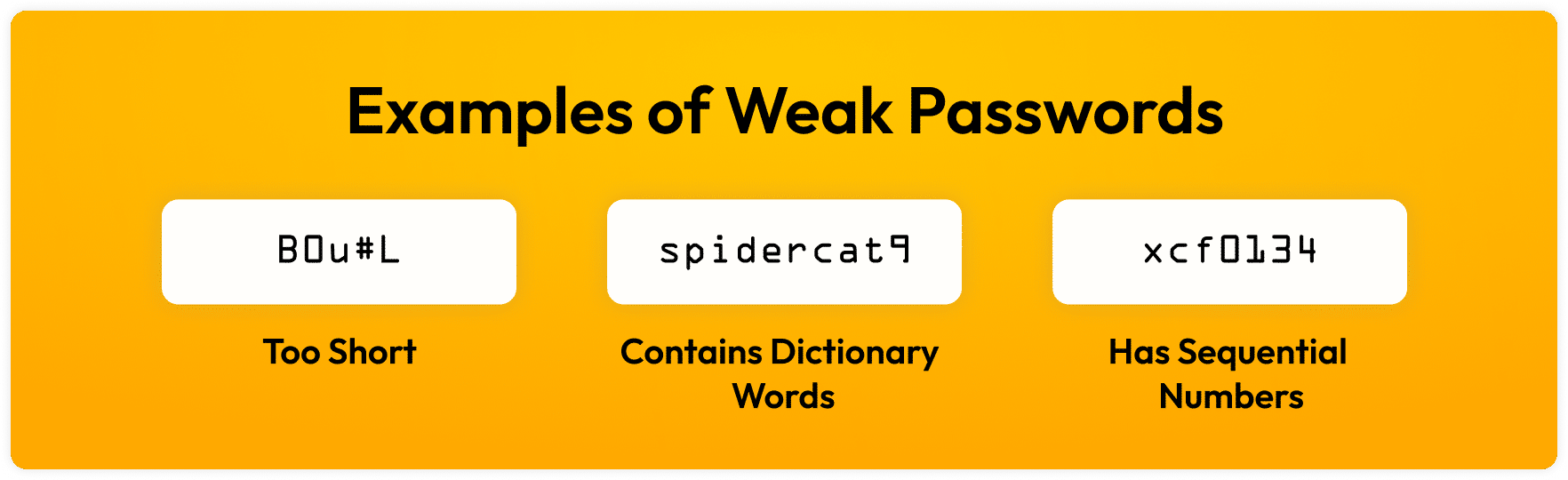
Common Password Mistakes That Put Websites at Risk
Before we talk prevention, let’s identify the most common issues:
-
Short passwords (under 12 characters)
-
Common words or patterns (e.g.,
password123,admin2024) -
Reused passwords across email, hosting, CMS, and social accounts
-
Shared login credentials among team members
-
No protection against brute-force attacks
-
Storing passwords in plain text or insecure files
Any one of these mistakes can be enough to compromise your website.
Step-by-Step Guide: How to Prevent a Weak Password From Breaking Your Website
Step 1: Use Long, Unique Passwords Everywhere
Password length matters more than complexity alone.
Best practice:
-
Minimum of 14–16 characters
-
Unique for every account
-
Avoid personal details (names, birthdays, brand names)
Good example:
Fence!Orbit7Maple$River
Bad example:
Website123
Long passwords dramatically reduce the success of brute-force attacks.
Step 2: Stop Reusing Passwords (Seriously)
Password reuse is one of the biggest security risks for website owners.
If one service is breached and your password is reused:
-
Hackers will try it on your hosting account
-
Then your CMS admin panel
-
Then your email
This is called credential stuffing, and it’s highly effective.
Rule of thumb:
Every login—hosting, CMS, database, FTP, email—gets its own password.
Step 3: Use a Password Manager
Remembering dozens of strong passwords isn’t realistic without help.
A password manager:
-
Generates strong, random passwords
-
Stores them securely (encrypted)
-
Autofills logins safely
-
Reduces phishing risks
Popular options include browser-based managers and dedicated apps. The key benefit is security without inconvenience.
If you manage a team, password managers also allow secure sharing without revealing the actual password.
Step 4: Enable Two-Factor Authentication (2FA)
Even the strongest password can be compromised. Two-factor authentication adds a critical second layer.
With 2FA enabled, users must provide:
-
Something they know (password)
-
Something they have (code, app, or device)
This means a stolen password alone is useless.
Enable 2FA on:
-
Website admin dashboards
-
Hosting control panels
-
Email accounts
-
Cloud services and backups
This single step can stop the vast majority of automated attacks.

Step 5: Limit Login Attempts and Monitor Access
Attackers often rely on brute-force attacks, trying thousands of passwords until one works.
You can block this by:
-
Limiting login attempts
-
Temporarily locking accounts after failures
-
Using CAPTCHA or bot detection
-
Logging login activity
Many CMS platforms offer built-in or plugin-based solutions for this.
Monitoring login attempts also helps you detect suspicious behavior early—before damage occurs.
Step 6: Use Role-Based Access (Not Shared Logins)
Shared passwords are dangerous and untraceable.
Instead:
-
Give each user their own login
-
Assign only the permissions they need
-
Remove access immediately when no longer required
This approach improves accountability and reduces the risk of accidental or malicious misuse.
Step 7: Secure Password Storage and Transmission
If you manage a custom website or application, password handling on the backend matters.
Never:
-
Store passwords in plain text
-
Email passwords to users
-
Log passwords in error reports
Always:
-
Use strong hashing algorithms
-
Enforce HTTPS site-wide
-
Encourage password resets instead of password sharing
Even if attackers access your database, properly stored passwords remain protected.
Step 8: Educate Your Team and Users
Technology alone isn’t enough—people are part of your security system.
Make sure users understand:
-
Why strong passwords matter
-
How to recognize phishing attempts
-
When and how to reset credentials
Clear password guidelines and regular reminders can prevent costly mistakes.
What Happens After a Password-Based Website Breach?

If a weak password leads to a breach, the consequences can include:
-
Loss of customer trust
-
Downtime and lost revenue
-
SEO penalties from malware warnings
-
Legal or compliance issues
-
Costly recovery and cleanup efforts
Recovering from a breach often takes far more time and money than preventing one.
Frequently Asked Questions (FAQs)
How often should website passwords be changed?
-
Immediately after a suspected breach
-
When a user leaves your organization
-
Periodically for high-risk accounts
Frequent forced changes aren’t always necessary if passwords are long, unique, and protected with 2FA.
Are password generators safe to use?
Yes—reputable password managers and generators are far safer than human-created passwords. They produce random combinations that are nearly impossible to guess.
Is two-factor authentication enough on its own?
No. 2FA is powerful, but it works best when combined with:
-
Strong, unique passwords
-
Limited login attempts
-
Secure access controls
Security is strongest when layered.
What’s the safest way to share website access with a developer?
The safest approach is:
-
Create a temporary user account
-
Assign minimal permissions
-
Use a password manager for sharing
-
Remove access once the work is complete
Avoid sending passwords via email or messaging apps.
Can a small website really be a target?
Absolutely. Automated attacks scan the internet for vulnerabilities, not company size. Small websites are often targeted because they’re less protected.
Final Thoughts
One weak password can break your website, but one smart security strategy can protect it.
By using long, unique passwords, enabling two-factor authentication, limiting access, and educating users, you dramatically reduce your risk—without making your site harder to manage.
Website security isn’t about paranoia. It’s about preparation.
Start strengthening your login practices today, and you’ll protect not just your website, but your users, reputation, and peace of mind. 🔐